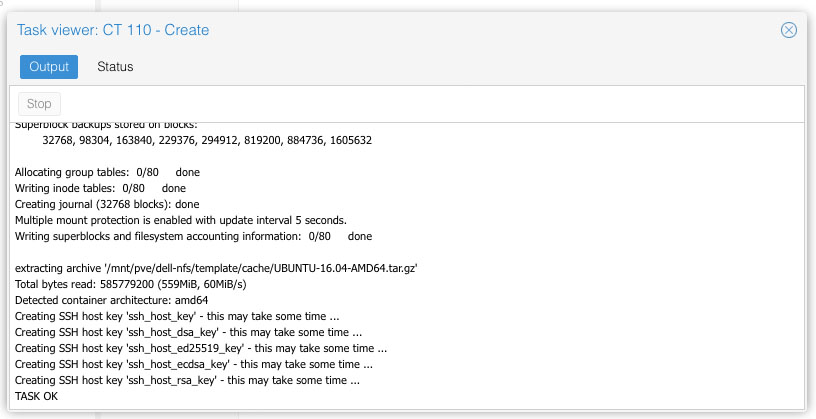
Create a KVM with custom HDD, RAM, CPU, etc. using CentOS 6 or 7 minimal
Disable selinux
Edit the /etc/selinux/config
vi /etc/selinux/config
Change SELINUX=enforcing to SELINUX=disabled
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=enforcing
# SELINUXTYPE= can take one of these two values:
# targeted - Targeted processes are protected,
# mls - Multi Level Security protection.
SELINUXTYPE=targeted
Turn off Firewall
(CentOS 7x)
systemctl stop firewalld
systemctl disable firewalld
yum -y install net-tools
Turn off Firewall
(CentOS 6x)
service iptables save
service iptables stop
chkconfig iptables off
Create a bash shell script seal.sh
vi /usr/src/seal.sh
Paste following script in the seal.sh file
#!/bin/bash
echo "Seal This Centos 6x and 7x Server"
yum clean all
> /etc/machie-id
rm -f /etc/ssh/ssh_host_rm -rf /root/.ssh/
rm -f /root/anaconda-ks.cfg
rm -f /root/.bash_history
unset HISTFILE
rm -f /var/log/boot.log
rm -f /var/log/cron
rm -f /var/log/dmesg
rm -f /var/log/grubby
rm -f /var/log/lastlog
rm -f /var/log/maillog
rm -f /var/log/messages
rm -f /var/log/secure
rm -f /var/log/spooler
rm -f /var/log/tallylog
rm -f /var/log/wpa_supplicant.log
rm -f /var/log/wtmp
rm -f /var/log/yum.log
rm -f /var/log/audit/audit.log
rm -f /var/log/tuned/tuned.logroot
Go to use /usr/src folder and make script executable
cd /usr/src
chmod +x seal.sh
Run seal.sh script
./seal.sh
Clear History
cat /dev/null > ~/.bash_history && history -c && exit
Generalize (seal) a Linux virtual machine using the sys-unconfig command before making it into a template. This prevents conflicts between virtual machines deployed from the template
sys-unconfig
Using Proxmox web interface Stop VM
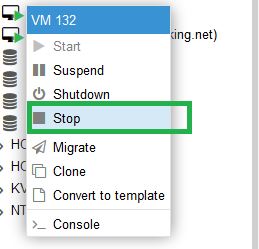
Next right click on the VM and Convert to Template
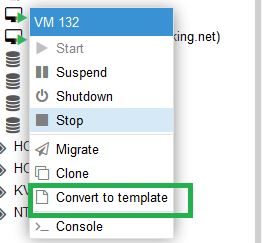
Your Custom CentOS Template is ready.